
VPN applied sciences have lengthy been the spine of distant entry, however in response to new ThreatLabz analysis, the safety dangers and efficiency challenges of VPNs could also be quickly altering the established order for enterprises.
The Zscaler ThreatLabz 2025 VPN Risk Report with Cybersecurity Insiders attracts on the insights of greater than 600 IT and safety professionals on the rising dangers and operational challenges posed by VPNs. It reveals that enterprises are actively grappling with the safety dangers, efficiency challenges, and operational complexity of VPNs. One key putting development: enterprises are starting to transition en masse to undertake zero belief options. Total, 65% of organizations plan to switch VPN companies throughout the yr, a 23% leap from final yr’s findings. In the meantime, 96% of organizations favor a zero belief method, and 81% plan to implement zero belief methods throughout the subsequent 12 months.
All of those shifts, in the meantime, occur throughout the context of an AI-enabled menace panorama. As a result of VPNs are internet-connected, it has develop into comparatively easy for attackers to make use of AI for automated recon focusing on VPN vulnerabilities. This may take the type of merely asking your favourite AI chatbot to return all present CVEs for VPN merchandise in use by an enterprise, that are then simply scanned over the general public web. When you think about that researchers have not too long ago found that tens of hundreds of public IP addresses hosted by a minimum of one of many largest safety suppliers are being actively scanned, doubtless by attackers, the crux of the issue for VPNs turns into clear: for those who’re reachable, you’re reachable.
The report analyzes these dangers within the context of enterprise issues, plans, and their adoption of zero belief methods to safe the hybrid workforce and allow safe connectivity to non-public functions. Under, this weblog publish discusses three key findings from the report underlying these crucial shifts. For full insights, evaluation, and finest practices, obtain the Zscaler ThreatLabz 2025 VPN Risk Report at present.
1. The widespread safety challenges of VPNs
Digital Personal Networks (VPNs) had been as soon as the gold commonplace for enabling safe distant entry. However as cyber threats evolve, VPNs have shifted from trusted instruments to main liabilities. Certainly, VPN vulnerabilities are proving irresistible for attackers; 56% of organizations reported VPN-exploited breaches reported final yr, a notable rise from the yr prior.
Such vulnerabilities pose a central problem. As a result of VPNs are internet-connected gadgets, menace actors can simply probe for impacted VPN infrastructure and exploit it earlier than any patch is launched or has been utilized. Not too long ago, CISA issued an advisory for impacted organizations to use safety updates for CVE-2025-22457, now a known-exploited crucial vulnerability that will enable unauthenticated attackers to attain distant code execution (RCE).
These gaps have develop into prime entry factors for ransomware campaigns, credential theft, and cyber espionage campaigns that may trigger widespread harm throughout networks. Certainly, a staggering 92% of respondents share issues that unpatched VPN flaws straight result in ransomware incidents—highlighting how troublesome it’s to constantly patch VPNs in time. In the meantime, 93% of respondents specific issues over backdoor vulnerabilities launched by third-party VPN connections, as attackers more and more exploit third-party credentials to breach networks undetected.
Mapping the rise of VPN CVEs from 2020-2025
In an effort to grasp the rise of VPN vulnerabilities, ThreatLabz additionally analyzed VPN Frequent Vulnerabilities and Exposures (CVEs) from 2020 to 2025 primarily based on information from the MITRE CVE Program. Normally, vulnerability reporting is an efficient factor, as speedy vulnerability disclosure and patching helps your entire ecosystem enhance cyber hygiene, enhance neighborhood collaboration, and shortly reply to new vectors of assault. No kind of software program is immune from vulnerabilities, nor ought to it’s anticipated to be.
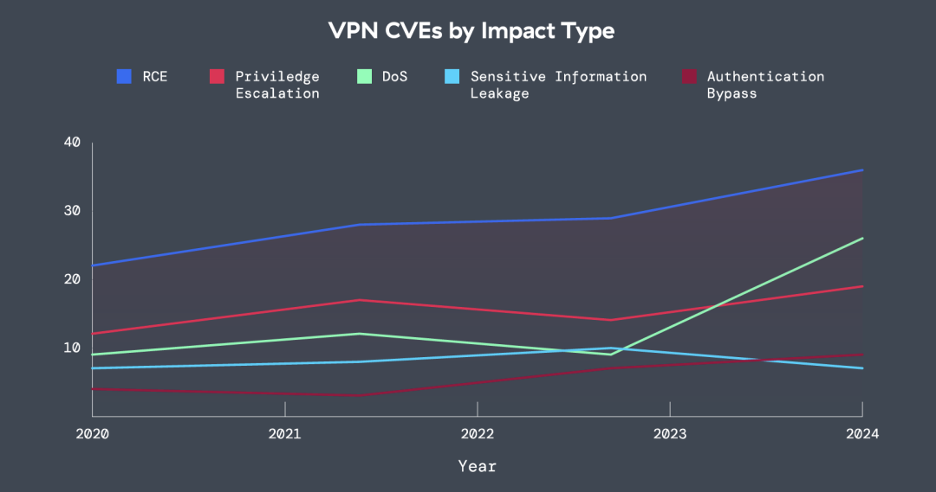
Zscaler
Determine 1: The impression kind of VPN CVEs from 2020-2024, overlaying distant code execution (RCE), privilege escalation, DoS, delicate data leakage, and authentication bypass.
How these CVEs are found and the data they comprise replicate adjustments within the evolving menace panorama. Within the case of VPNs, ThreatLabz discovered that not solely have VPN vulnerabilities elevated over time — partially reflecting their recognition through the post-COVID transition to hybrid work — however they’re typically extreme.
Over the pattern interval, VPN CVEs grew by 82.5% (word that early 2025 information has been eliminated for this portion of the evaluation). Up to now yr, roughly 60% of the vulnerabilities indicated a excessive or crucial CVSS rating — indicating a probably critical threat to impacted organizations. Furthermore, ThreatLabz discovered that vulnerabilities enabling distant code execution (RCE) had been essentially the most prevalent sort when it comes to the impression or capabilities they will grant to attackers. All these vulnerabilities are usually critical, as they will grant attackers the power to execute arbitrary code on the system. Put one other manner, removed from being innocuous, the majority of VPN CVEs are leaving their prospects susceptible to exploits that attackers can, and infrequently do, exploit.
As enterprises race to maintain tempo with advancing attacker sophistication, organizations are turning to different choices. Zero belief architectures are rising as the answer for filling these safety gaps. Not like VPNs, which depend on implicit belief and broad community entry, zero belief frameworks implement granular, identity-driven entry insurance policies that straight mitigate attacker motion inside networks — and take away the chance of internet- and network-connected belongings that may be simply scanned for and exploited by attackers.
2. Finish-user frustration driving enterprise decision-making
VPN inefficiencies aren’t only a downside for safety—they’re irritating customers. Sluggish connectivity, frequent disconnections, and complicated authentication processes have plagued VPN customers for years — and these challenges prime the record of end-user frustrations in our findings. In line with the report, these consumer expertise frustrations are more and more influencing IT methods, with enterprises trying to zero belief to ship safe entry with out efficiency challenges or compromises.
Zero belief fashions obtain this by bypassing centralized community dependencies in favor of direct, application-specific connections. The consequence? Staff achieve swift and seamless entry to the instruments they want, whereas IT groups can guarantee safety posture checks and coverage enforcement in real-time. Unsurprisingly, satisfaction with zero belief options spans each finish customers and IT groups, solidifying this method as the following evolution of safe entry.
3. 81% of organizations are actively transitioning to Zero Belief frameworks
Because of these traits, a widespread realization is remodeling cybersecurity methods: zero belief isn’t simply conceptual anymore—it’s elementary. With 81% of organizations actively implementing zero belief frameworks throughout the subsequent yr, enterprises are pivoting away from legacy VPN programs that fail to fulfill the distant entry calls for of companies at present. This shift marks a key transition from viewing zero belief as a theoretical ideally suited to adopting it as a sensible resolution.
What makes zero belief the favored method? Not like VPNs, which generally grant broad community entry primarily based on implicit belief, zero belief operates on the precept of “by no means belief, at all times confirm.” Zero belief permits extremely granular entry controls to non-public functions, sturdy id verification, and steady monitoring, delivering efficient safety for distributed workforces and hybrid IT environments. Normally, enterprises which have transitioned to zero belief from a VPN expertise discovered improved safety and compliance as the first benefit (76%) — reinforcing how zero belief replaces implicit community entry and reduces publicity to ransomware, credential theft, and lateral motion dangers. Coupled with beneficial properties in scalability, compliance, and operational simplicity, it’s more and more clear why zero belief architectures are quickly changing VPNs.
Get the report
For enterprises looking for perspective on VPN and distant entry, the ThreatLabz 2025 VPN Threat Report gives key insights. Download your copy for crucial insights into:
- Enterprise safety and operational challenges of VPN
- Important finest observe for securing the hybrid workforce
- Peer insights into the zero belief transition
- VPN predictions for 2025 and past